Security Issues with Mobile Ad-Hoc Networks
When we think about computer networks the idea of structured planned and properly segmented arrangement of computer devices comes to mind. The word ad-hoc means 'not pre-planned' before it happens. In Mobile Ad-hoc networks (MANETS ) the word carries the same connotation.
MANETS can be likened to a scrabble game. Any player (user) can place tiles in any part of the board (connect a node at any point) as long as they connect to one existing tile (connection to the network). As such the tiles of the board can easily take any shape (topology) as nodes continue to join the network.
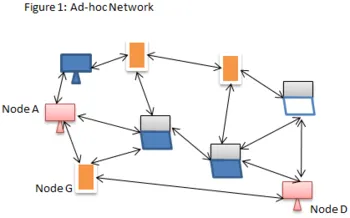
A Mobile Ad-hoc network (also known as a wireless ad-hoc network) is defined as network designed without any formal structured configuration, as seen in Figure 1. Nodes connected to the network can be configured dynamically without following any formally pre-defined top-down architecture as characterized by conventional networks (see Figure 2). Nodes are rather configured in a very free and autonomous manner. The general 'non-structure' is a decentralized arrangement of nodes. It is particularly popular in situations with no pre-existing network infrastructure by allowing nodes seamless connectivity to it.

|
|
MANETs are characterized by the following:
With no top-down pre-defined centralized structure, nodes are allowed to connect or disconnect dynamically at any point in the network making the structure of the topology dynamic. This means that the shape or structure of of the network is constantly changing according to user requirements.
The nodes that operate within the MANET have low system specifications with small memory sizes, lower CPU speeds and storage.
Nodes connected to the network communicate directly with each other, as long as communicating nodes are within the required radio range of each other. If they are not, then nearby nodes will act as routers to forward the data packets to the destination nodes. This is called a multi-hop environment. Each node therefore has a wireless interface to facilitate this communication.
For example looking at Figure 1. If node A has to communicate with node D which is out of its range, then node G can step in as an intermediary router to forward the data packets thereby forming an ad-hoc network. This also means that with this topology each node can act as a router or a host carrying a routing table in order to forward data packets.
The constantly changing nature of the network topology coupled with data transmission in open medium makes it highly susceptible to attacks. Security issues with respect to data confidentiality, availability of systems and applications, authentication, system integrity are just as threatening as in conventional networks. Vulnerabilities can lead to message eavesdropping, injection of fake messages, denial of service attack or poor monitoring of routing information.
MANETs are susceptible to both internal and external attacks.
Internal attacks target the nodes directly as well as the networking interface links which facilitate seamless transmission. The routing tables which are at the core of direct node communication are prime targets. With each node hosting a copy of the routing table detecting these types of attacks can be very difficult. Incorrect routing information once broadcast and adopted around the network from the corrupt nodes, makes isolating the culprit more difficult.
External attacks target the performance of the network. These include network congestions, denial of Service (DoS) attacks and corrupt routing information.
With its lack of prior organization and centralization the security issues in a MANET differ from those found in other conventional network infrastructures and therefore require different security mechanisms. A number of 'first line of defense' security measures can be implemented to reduce the occurrence of attacks.