Spread Spectrum Modulation
A collective class of signaling techniques are employed before transmitting a signal to provide a secure communication, known as the Spread Spectrum Modulation. The main advantage of spread spectrum communication technique is to prevent “interference” whether it is intentional or unintentional.
The signals modulated with these techniques are hard to interfere and cannot be jammed. An intruder with no official access is never allowed to crack them. Hence, these techniques are used for military purposes. These spread spectrum signals transmit at low power density and has a wide spread of signals.
A coded sequence of 1s and 0s with certain auto-correlation properties, called as Pseudo-Noise coding sequence is used in spread spectrum techniques. It is a maximum-length sequence, which is a type of cyclic code.
Both the Narrow band and Spread spectrum signals can be understood easily by observing their frequency spectrum as shown in the following figures.
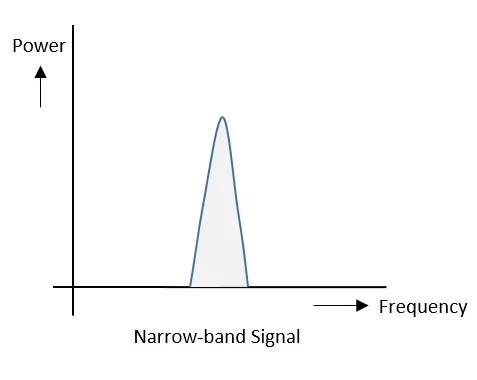
The Narrow-band signals have the signal strength concentrated as shown in the following frequency spectrum figure.

Following are some of its features −
Though the features are good, these signals are prone to interference.
The spread spectrum signals have the signal strength distributed as shown in the following frequency spectrum figure.
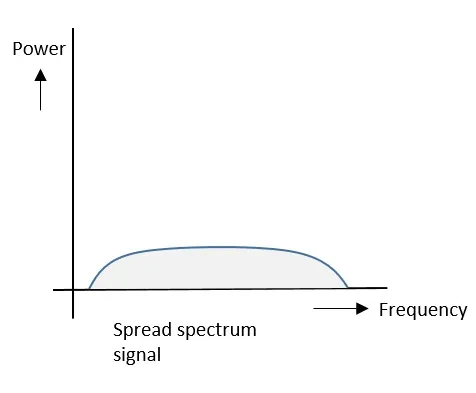
Following are some of its features −
With these features, the spread spectrum signals are highly resistant to interference or jamming. Since multiple users can share the same spread spectrum bandwidth without interfering with one another, these can be called as multiple access techniques.
Spread spectrum multiple access techniques uses signals which have a transmission bandwidth of a magnitude greater than the minimum required RF bandwidth.
These are of two types.
This is frequency hopping technique, where the users are made to change the frequencies of usage, from one to another in a specified time interval, hence called as frequency hopping. For example, a frequency was allotted to sender 1 for a particular period of time. Now, after a while, sender 1 hops to the other frequency and sender 2 uses the first frequency, which was previously used by sender 1. This is called as frequency reuse.
The frequencies of the data are hopped from one to another in order to provide a secure transmission. The amount of time spent on each frequency hop is called as Dwell time.
Whenever a user wants to send data using this DSSS technique, each and every bit of the user data is multiplied by a secret code, called as chipping code. This chipping code is nothing but the spreading code which is multiplied with the original message and transmitted. The receiver uses the same code to retrieve the original message.
Both the spread spectrum techniques are popular for their characteristics. To have a clear understanding, let us take a look at their comparisons.
FHSS | DSSS / CDMA |
Multiple frequencies are used | Single frequency is used |
Hard to find the user’s frequency at any instant of time | User frequency, once allotted is always the same |
Frequency reuse is allowed | Frequency reuse is not allowed |
Sender need not wait | Sender has to wait if the spectrum is busy |
Power strength of the signal is high | Power strength of the signal is low |
Stronger and penetrates through the obstacles | It is weaker compared to FHSS |
It is never affected by interference | It can be affected by interference |
It is cheaper | It is expensive |
This is the commonly used technique | This technique is not frequently used |
Following are the advantages of spread spectrum −
Although spread spectrum techniques were originally designed for military uses, they are now being used widely for commercial purpose.