Documenting the Results of Risk Assessment
· By the end of the Risk Assessment process, you probably have a collection of long lists of information assets with data about each of them.
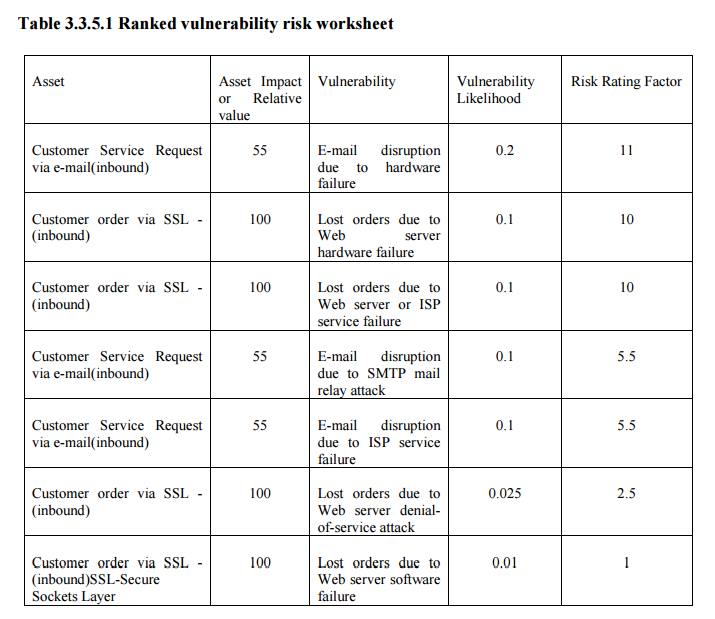
· The goal of this process is to identify the information assets that have specific vulnerabilities and list them, ranked according to those most needing protection. You should also have collected some information about the controls that are already in place.
· The final summarized document is the ranked vulnerability risk worksheet, a sample of which is shown in the following table.
Ranked vulnerability risk worksheet
