Risk Response
Taking Action
Following identification and analysis of project risks, Project Managers and project teams must act. Accountability demands a response to identified project risks. Focus should be directed toward risks of most significance. Effective project risk management can shift the odds in favor of project success.
Early in project development, activities and information can seem chaotic, coming to us from multiple directions and multiple sources. Risk management provides a structured and disciplined way to document, evaluate, and analyze the information, so we emerge with a well-organized and prioritized list of project risks. This prioritization rescues us from indecision, with information we can use to direct our project risk management resources.
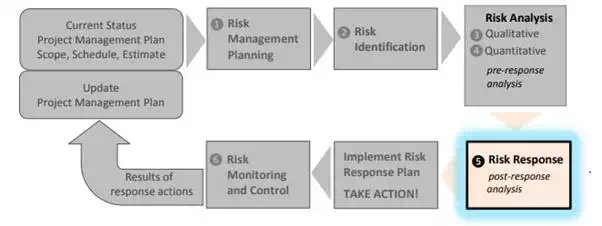
In order to maximize the benefits of project risk management, we must incorporate the project risk management activities into our Project Management Plan and work activities. This means building risk management activities into our Work Breakdown Structure (WBS). WSDOT has a readymade WBS in the form of its Master Deliverables List (MDL) to help ensure our project work plans are comprehensive, consistent, and complete. As shown above, the risk management steps include: Risk Management Planning, Risk Identification, Qualitative Risk Analysis, Quantitative Risk Analysis, Risk Response, and Risk Monitoring and Control.
Risk response requires effort to develop and implement response actions; we must plan for expending this effort following the results of our risk analysis. To this end, we have a number of tools readily available, including the Risk Management Planning spreadsheet
The Project Risk Manager should pay special attention to highimpact, low-probability risks. Team awareness and conscious monitoring of these risks can be accomplished via team meetings, informing upper management, and seeking counsel from appropriate experts.
Actions in Response to Risks
Risk Response
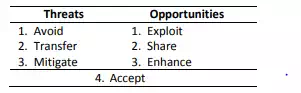
AVOID (threats)
Avoidance actions include: changing the project scope to eliminate a threat; clarifying requirements, obtaining information, improving communication, or acquiring expertise. (Source: Project Management Body of Knowledge [PMBOK])
There are two types of action: (1) remove the cause of the risk (risk trigger), or (2) execute the project in a different way while still aiming to achieve project objectives. Not all risks can be avoided or eliminated, and for others this approach may be too expensive or time-consuming, but this should be the first strategy considered for each risk.
EXPLOIT (opportunities)
The opposite of avoid, this strategy is to ensure a positive impact, or realize an opportunity. Take action to make the opportunity happen; such response actions include: assigning more talented resources to a project to reduce time to completion and/or providing better quality than originally planned. (PMBOK)
Eliminate the uncertainty associated with a particular upside risk. An opportunity is defined as a risk event that, if it occurs, will have a positive effect on achievement of project objectives. Avoid and Exploit are the most aggressive of the response strategies and should be reserved for those “golden opportunities” with high probability and impacts.
TRANSFER (threats)
Transferring a threat does not eliminate it—the threat still exists; however, it is owned and managed by another party. Transferring risk can be an effective way to deal with financial risk exposure. Transferring project risk involves payment of a risk premium to the party taking the risk; for example, insurance, performance bonds, or warranties. Contracts may be used to transfer specified risks to another party.
Transferring risk involves finding another party who is willing to take responsibility for its management, and who will bear the liability of the risk should it occur. The aim is to ensure that the risk is owned and managed by the party best able to deal with it effectively. Risk transfer usually involves payment of a premium, and the cost-effectiveness of this must be considered when deciding whether to adopt a transfer strategy.
SHARE (opportunities)
Sharing a positive risk involves allocating ownership to a third party who is best able to capture the opportunity for the benefit of the project. Examples of sharing actions include forming risk-sharing partnerships, teams, or joint ventures, which can be established with the express purpose of managing opportunities.
Allocating risk ownership for an opportunity to another party who is best able to handle it, in terms of maximizing probability of occurrence and increasing potential benefits if it does occur. Transferring threats and sharing opportunities are similar in that a third party is used; those to whom threats are transferred take on the liability and those to whom opportunities are allocated should also be allowed to share in the potential benefits.
MITIGATE – or reduce (threats)
Risk mitigation implies a reduction in the probability and/or impact of an adverse risk event to an acceptable threshold. Taking early action is often more effective to repair than trying to repair the damage after the risk has occurred. Examples of mitigation strategies include: adopting less complex processes, conducting more tests and/or field investigations, developing a prototype. Measures to address impacts include: targeting linkages that determine the severity, such as designing redundancy into a subsystem, may reduce the impact from a failure of the original component.
Mitigation or acceptance are the strategies most often used since the number of threats that can be addressed by avoidance or transfer are usually limited. Preventive responses are better than curative responses because they are more proactive and if successful can lead to risk avoidance. Preventive responses tackle the causes of the risk; where it is not possible to reduce probability, a mitigation response should address the adverse impact, targeting the drivers that determine the extent of the severity.
ENHANCE (opportunities)
This response modifies the “size” of an opportunity by increasing probability and/or impact. Seeking to facilitate or strengthen the cause of the opportunity, and proactively targeting and reinforcing its trigger conditions. Impact drivers can also be targeted, seeking to increase the project’s susceptibility to the opportunity.
This response aims to modify the “size” of the positive risk. We enhance the opportunity by increasing the probability and/or impact of an opportunity thereby maximizing benefits realized for the project. If the probability can be increased to 100%, this is effectively an exploit response.
ACCEPT
The term “accept” refers to risks that remain after response actions and/or for which response is not cost-effective are accepted; risks that are uncontrollable (no response actions are practical) are also accepted.
Ultimately, it is not possible to eliminate all threats or take advantage of all opportunities; we can document them and at least provide awareness that these exist and have been identified; some term this “passive acceptance.” In some cases, in some industries, a contingency reserve is established to deal with the aggregate residual risk that has been accepted; some term this “active acceptance.” As we continue through project development, the project risk profile will change. As we successfully respond to risks and our project knowledge increases, our risk exposure will diminish.