Classifying Networks by Component Roles
Another method used to classify networks focuses on the roles the networked computers play in the network’s operation, and more specifically on which computer controls that operation. There are two basic types of role classifications for networks—peer-to-peer networks and server-based networks. The difference between the two revolves around which computer is in charge of the network. A third classification, client-based networks, has come into existence because of the increased capabilities of the typical client computer.
Peer-to-Peer Networks
A peer is considered an equal. All computers on a peer-to-peer network can be considered equals, as shown in Figure 1.9. That is to say, no one computer is in charge of the network’s operation. Each computer controls its own information and is capable of functioning as either a client or a server depending on which is needed at the time. Peer-to-peer networks are popular as home networks and for use in small companies because they are inexpensive and easy to install. Most operating systems (the software that runs the basic computer functionality) come with peer-to-peer networking capability built in. The only other cost involved with setting up a peer-to-peer network comes into play if a computer does not have a network interface card, or NIC (the device that physically connects your computer to your network’s cabling), already installed. Typical initial peer-to-peer networking involves no security measures. Rather, each peer simply shares its resources and allows others open access to them. In fact, a peer-to-peer network becomes difficult to manage when more and more security is added to the resources. This is because users control their own security by adding password protection to each share they create. Shares are any resources users control on their computers, such as document folders, printers, and other peripherals. Each shared resource can actually have its own password. Someone wanting access to numerous shared resources has to remember many passwords. Security on a peerto-peer network can quickly become complex and confusing
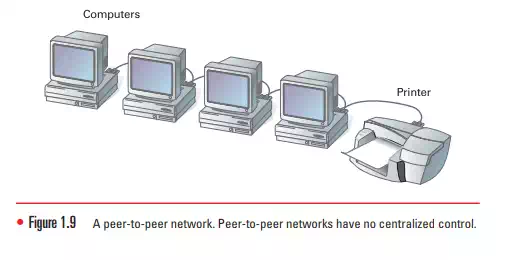
While peer-to-peer networks are inexpensive to set up, they are extremely limited in scope. The accepted maximum number of peers that can operate on a peer-to-peer network is ten. They are, therefore, not appropriate for larger, more secure networks.
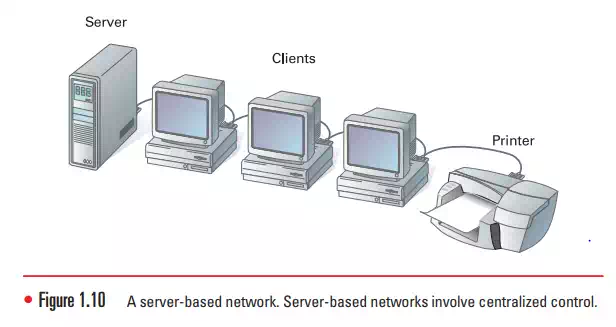
Server-Based Networks
Unlike peer-to-peer networks that operate without central control and are difficult to secure, a server-based network offers centralized control and is designed for secured operations, as shown in Figure 1.10. While there are still both clients and servers on a server-based network, a dedicated server controls the network. A dedicated server is one that, for all practical purposes, operates solely as a server.
A dedicated server on a server-based network services its network clients by storing data, applications, and other resources, and then providing access to those resources when called for by a client. When a client requests a resource such as a document, the server sends the whole resource (the document) over the network to the client, where it is processed and later returned to the server for continued storage.
Dedicated servers can also control the entire network’s security from one central location or share that control with other specially configured servers. This central network control also contributes to the economies of scale discussed under the “Facilitating Centralized Management” section earlier in this chapter (using similar equipment results in cheaper equipment prices and fewer training costs) and makes the server-based network the dominant networking model used in networks today.
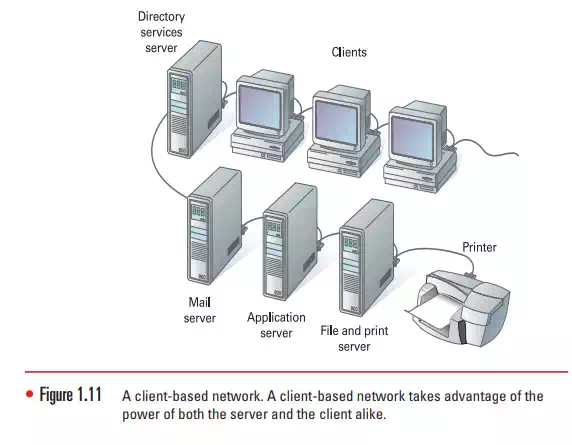
Client-Based Networks
Client-based networks are a further refinement to the concept of a serverbased network that relieves the heavy burden on the network’s capacity resulting from frequent server-performed transactions. A client-based network takes better advantage of the server’s powerful processors and of the increasingly powerful computers used in typical workstations. A client based network utilizes a client workstation’s power in processing some functions locally while requesting additional processing from a server whenever it is needed for increased speed.
Client-based network servers process requests from clients and return just the results, rather than sending the original resource to the client to be processed and returned after computations are complete. Client-based networks, therefore, take advantage of the powerful processing capabilities of both the client and the server, as shown in Figure 1.11. This type of arrangement may include application servers (where entire computer programs are shared from the server) and communications servers (where e-mail and other communications media are operated).