Digital Signature
A signature on a legal, financial or any other document authenticates the document. A photocopy of that document does not count. For computerized documents, the conditions that a signed document must hold are—(1) The receiver is able to verify the sender (as claimed), (2) The sender cannot later repudiate the contents of the message, (3) The receiver cannot concoct the message himself. A digital signature is used to sign a computerized document. The properties of a digital signature are same as that of ordinary signature on a paper. Digital signatures are easy for a user to produce, but difficult for anyone else to forge. Digital signatures can be permanently tied to the content of the message being signed and then cannot be moved from one document to another, as such an attempt will be detectable.
Digital signature scheme is a type of asymmetric cryptography. Digital signatures use the public- key cryptography, which employs two keys—private key and public key. The digital signature scheme typically consists of three algorithms:
· Key generation algorithm—The algorithm outputs private key and a corresponding public key.
· Signing algorithm—It takes, message + private key, as input, and, outputs a digital signature.
· Signature verifying algorithm—It takes, message + public key + digital signature, as input, and, accepts or rejects digital signature.
The use of digital signatures typically consists of two processes—Digital signature creation and Digital signature verification. Two methods are commonly used for creation and verification of the digital signatures.
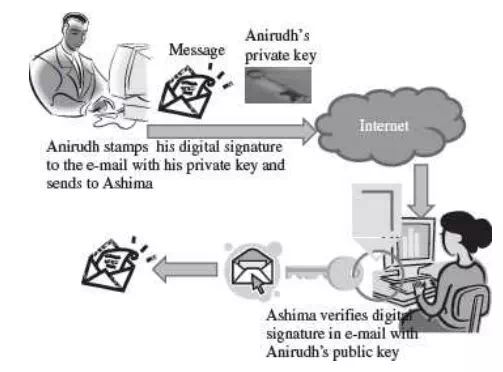
Digital signature
· In the First Method, the signer has a private key and a public key. For a message to be sent, the signer generates the digital signature by using the private key to encrypt the message. The digital signature along with the message is sent to the receiver. The receiver uses the public key (known to the receiver) to verify the digital signature. This method is used to verify the digital signature. Even if many people may know the public key of a given signer and use it to verify that signer’s signature, they cannot generate the signer’s private key and use it to forge digital signatures.
· In the Second Method, a hash function is used for digital signature. It works as follows:
I. Digital signature creation
![]() The signer has a private key and a public key.
The signer has a private key and a public key.
![]() For a message to be sent, a hash function in the
signer’s software computes an “original hash result” unique to the “original
message”.
For a message to be sent, a hash function in the
signer’s software computes an “original hash result” unique to the “original
message”.
![]() The signer uses signing algorithm to generate a
unique digital signature. “original hash result” + signer’s private key =
digital signature.
The signer uses signing algorithm to generate a
unique digital signature. “original hash result” + signer’s private key =
digital signature.
I. The generated digital signature is attached to its “original message” and transmitted with it.
II. Digital signature verification uses digital signature, “received message” and signer’s public key.
· A “new hash result” of the “received message” is computed using the same hash function used for the creation of the digital signature.
· The verification software verifies two things—whether the digital signature was created using the signer’s private key and, whether the “received message” is unaltered. For this, the signer’s public key verifies the digital signature (signer’s public key can only verify a digital signature created with the signer’s private key). Once the key is verified, the “original hash result” of the digital signature is available. It compares “original hash result” with the “new hash result”. When the verification software verifies both the steps as “true”; it verifies the received message.
The digital signature accomplish the effects desired of a signature for many legal purposes:
· Signer Authentication: The digital signature cannot be forged, unless the signer loses control of the private key.
· Message Authentication: The digital signature verification reveals any tampering, since the comparison of the hash results shows whether the message is the same as when signed.
· Efficiency. The digital signatures yield a high degree of assurance (as compared to paper methods like checking specimen signatures) without adding much to the resources required for processing.
The likelihood of malfunction or a security problem in a digital signature cryptosystem, designed and implemented as prescribed in the industry standards, is extremely remote. Digital signatures have been accepted in several national and international standards developed in cooperation with and accepted by many corporations, banks, and government agencies. In India “Information Technology Act 2000” provides legal recognition for transactions carried out by means of electronic data interchange and other means of electronic communication, commonly referred to as “electronic commerce”, which involves the use of alternatives to paper-based methods of communication and storage of information, to facilitate electronic filing of documents with the government agencies.