Cryptography
Cryptography is the science of writing information in a “hidden” or “secret” form and is an ancient art. Cryptography is necessary when communicating data over any network, particularly the Internet. It protects the data in transit and also the data stored on the disk. Some terms commonly used in cryptography are:
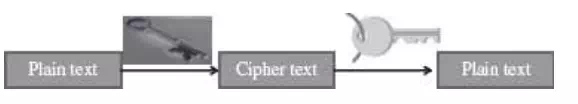
· Plaintext is the original message that is an input, i.e. unencrypted data.
· Cipher and Code—Cipher is a bit-by-bit or character-by-character transformation without regard to the meaning of the message. Code replaces one word with another word or symbol. Codes are not used any more.
· Cipher text—It is the coded message or the encrypted data.
· Encryption—It is the process of converting plaintext to cipher text, using an encryption algorithm.
· Decryption—It is the reverse of encryption, i.e. converting cipher text to plaintext, using a decryption algorithm.
Cryptography uses different schemes for the encryption of data. These schemes constitute a pair of algorithms which creates the encryption and decryption, and a key.
Key is a secret parameter (string of bits) for a specific message exchange context. Keys are important, as algorithms without keys are not useful. The encrypted data cannot be accessed without the appropriate key. The size of key is also important. The larger the key, the harder it is to crack a block of encrypted data. The algorithms differ based on the number of keys that are used for encryption and decryption. The three cryptographic schemes are as follows:
· Secret Key Cryptography (SKC): Uses a single key for both encryption and decryption,
· Public Key Cryptography (PKC): Uses one key for encryption and another for decryption,
· Hash Functions: Uses a mathematical transformation to irreversibly encrypt information.
In all these schemes, algorithms encrypt the plaintext into cipher text, which in turn is decrypted into plaintext.
Secret Key Cryptography
Secret key cryptography uses a single key for both encryption and decryption. The sender uses the key to encrypt the plaintext and sends the cipher text to the receiver. The receiver applies the same key to decrypt the message and recover the plaintext. Since a single key is used for encryption and decryption, secret key cryptography is also called symmetric encryption.

Secret key cryptography (uses a single key for both encryption and decryption)
· Secret key cryptography scheme are generally categorized as stream ciphers or block ciphers.
· Stream ciphers operate on a single bit (byte or computer word) at a time and implement some form of feedback mechanism so that the key is constantly changing
· Block cipher encrypts one block of data at a time using the same key on each block. In general, the same plaintext block will always encrypt to the same cipher text when using a same key in a block cipher.
· Secret key cryptography requires that the key must be known to both the sender and the receiver. The drawback of using this approach is the distribution of the key. Any person who has the key can use it to decrypt a message. So, the key must be sent securely to the receiver, which is a problem if the receiver and the sender are at different physical locations.
· Data Encryption Standard (DES) and Advanced Encryption Standard (AES) are some of the secret key cryptography algorithms that are in use nowadays.
Public-Key Cryptography
· Public-key cryptography facilitates secure communication over a non-secure communication channel without having to share a secret key.
· Public-key cryptography uses two keys—one public key and one private key.
· The public key can be shared freely and may be known publicly.
· The private key is never revealed to anyone and is kept secret.
· The two keys are mathematically related although knowledge of one key does not allow someone to easily determine the other key.
Public key cryptography (uses two keys—one for encryption and other for decryption)
· The plaintext can be encrypted using the public key and decrypted with the private key and conversely the plaintext can be encrypted with the private key and decrypted with the public key. Both keys are required for the process to work (Figure 14.7). Because a pair of keys is required for encryption and decryption; public-key cryptography is also called asymmetric encryption.
· Rivest, Shamir, Adleman (RSA) is the first and the most common public-key cryptography algorithm in use today. It is used in several software products for key exchange, digital signatures, or encryption of small blocks of data. The Digital Signature Algorithm (DSA) is used to provide digital signature capability for the authentication of messages.