Security Threat And Security Attack
A threat is a potential violation of security and causes harm. A threat can be a malicious program, a natural disaster or a thief. Vulnerability is a weakness of system that is left unprotected. Systems that are vulnerable are exposed to threats. Threat is a possible danger that might exploit vulnerability; the actions that cause it to occur are the security attacks. For example, if we leave the house lock open—it is vulnerable to theft; an intruder in our locality (might exploit the open lock)is a security threat; the intruder comes to know of the open lock and gets inside the house—This is a security attack.
A security attack may be a passive attack or an active attack.
The aim of a passive attack is to get information from the system, but it does not affect the system resources. Passive attacks are similar to eavesdropping. Passive attacks may analyse the traffic to find the nature of communication that is taking place, or, release the contents of the message to a person other than the intended receiver of the message. Passive attacks are difficult to detect because they do not involve any alteration of the data. Thus, the emphasis in dealing with passive attacks is on prevention rather than detection.
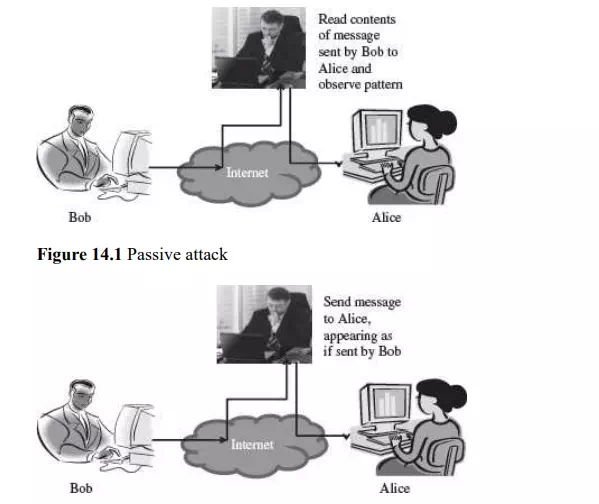
Active attack (masquerade)
· An active attack tries to alter the system resources or affect its operations. Active attack may modify the data or create a false data. An active attack may be a masquerade (an entity pretends to be someone else), replay (capture events and replay them), modification of messages, and denial of service. Active attacks are difficult to prevent. However, an attempt is made to detect an active attack and recover from them.
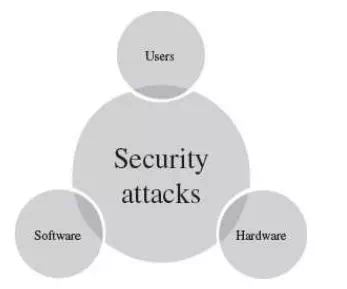
Security attacks can be on users, computer hardware and computer software.
· Attacks on users could be to the identity of user and to the privacy of user. Identity attacks result in someone else acting on your behalf by using personal information like password, PIN number in an ATM, credit card number, social security number etc. Attacks on the privacy of user involve tracking of users habits and actions—the website user visits, the buying habit of the user etc. Cookies and spam mails are used for attacking the privacy of users.
· Attacks on computer hardware could be due to a natural calamity like floods or earthquakes; due to power related problems like power fluctuations etc.; or by destructive actions of a burglar.
· Software attacks harm the data stored in the computer. Software attacks may be due to malicious software, or, due to hacking. Malicious software or malware is a software code included into the system with a purpose to harm the system. Hacking is intruding into another computer or network to perform an illegal act.
Security attacks